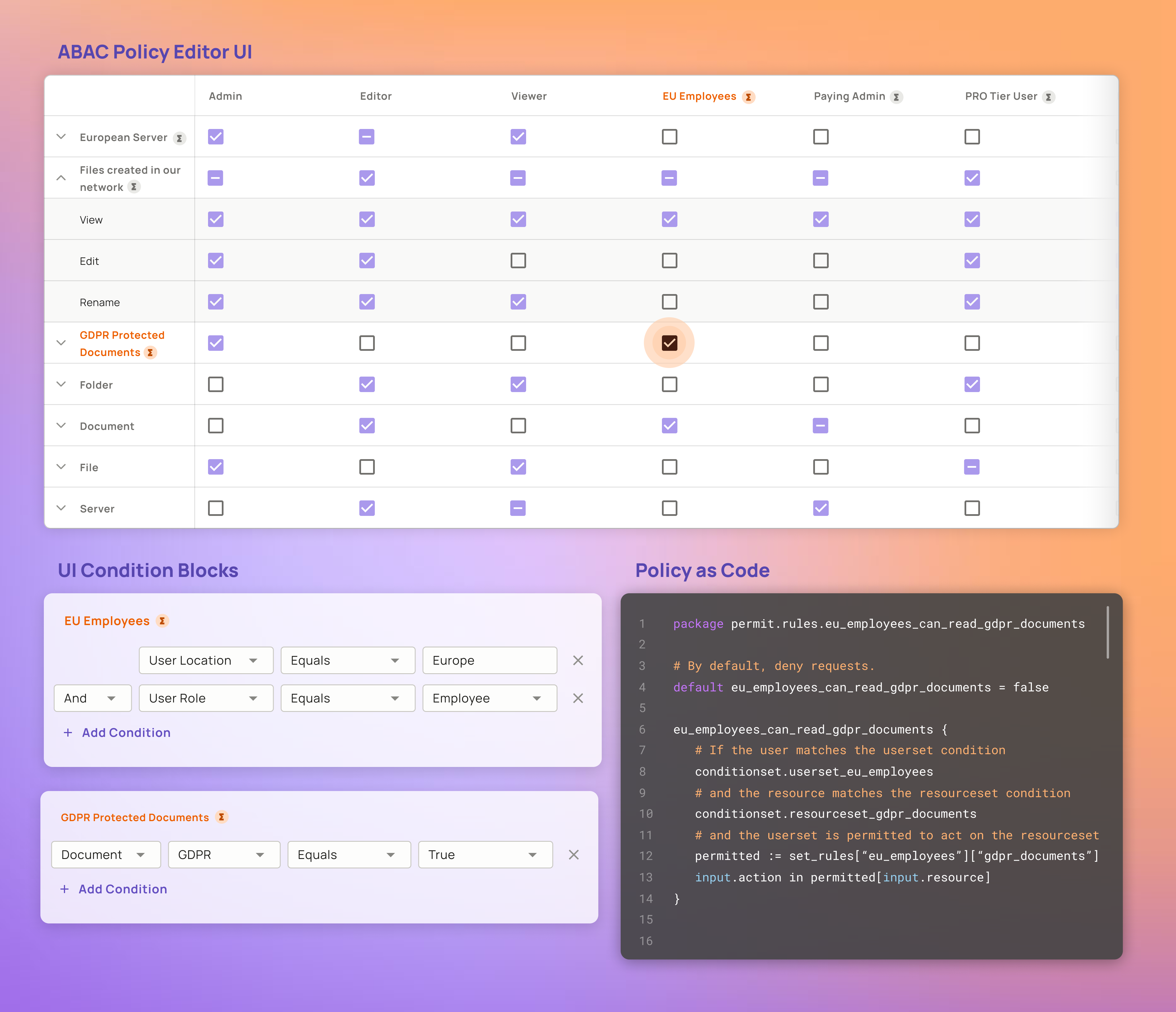
Limiting the visibility of sensitive data items through attribute-based access control (ABAC) - PegaWiki

Five Cornerstones of ABAC: Policy, Subject, Object, Operation Type and... | Download Scientific Diagram

Five Cornerstones of ABAC: Policy, Subject, Object, Operation Type and... | Download Scientific Diagram

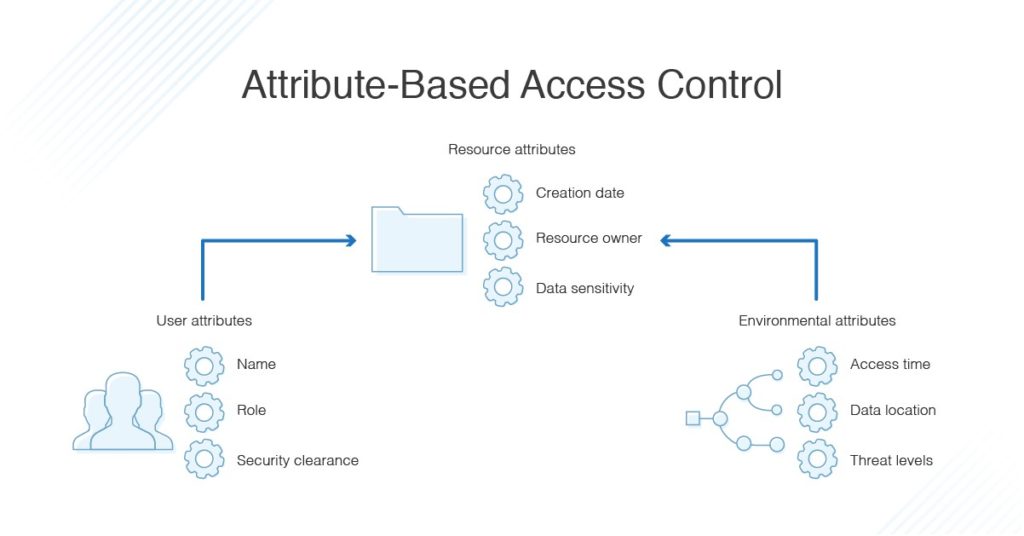
Figure 4 from Guide to Attribute Based Access Control (ABAC) Definition and Considerations | Semantic Scholar

Research Summary: Efficient Attribute-Based Smart Contract Access Control Enhanced by Reputation Assessment - Auditing and Security - Smart Contract Research Forum


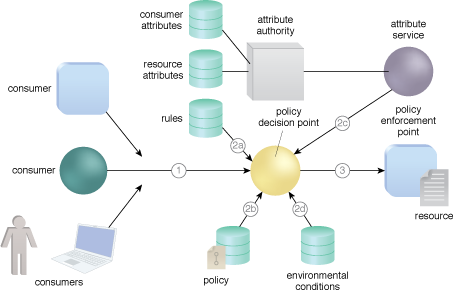




/An%20open%20source%20policy%20language%20for%20Attribute-Stream%20Based%20Access%20Control%20(ASBAC)/attribute-stream_based_access_control_mechanism.png)